WebSpy - Protocol inspection tool
Are you a web designer who doesn't really understand how the HTTP protocol works? Do you want to load test your web site to see how many users it can handle? Do you want to check to see what ports are open on your computer? Check out the features that WebSpy has to offer!
WebSpy was written a an internal utility to help with web programming. Firstly, it was written for the purpose of inspecting the information being submitted to the web server. Secondly, the ability to load test a site was needed to review the performance capabilities of various solutions (Perl, PHP, C/C++). This was important in determining which technology to utilize for our high traffic sites. And finally, the Port Scanning features were added just for kicks.
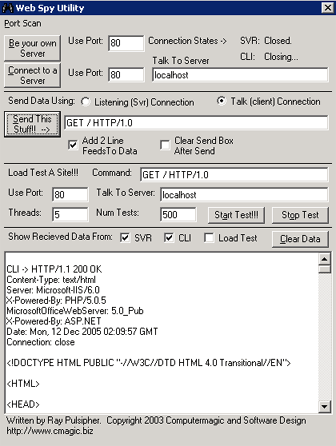
WebSpy is a generic utility that can communicate with any service that utilizes a text based protocol. Use it to see the actual conversation that goes on in a web request. WebSpy is not a packet sniffer, it is your own link to communicating directly with a server or a client (e.g. web browser). With it you can be your own server, or talk to any server on the Internet. This is a great tool for testing and debugging your own custom applications. Check out the features below:
Ability to serve up content, type in your side of the conversation and watch the results appear on the connected client (e.g. web browser).
Connect to servers and communicate directly at the protocol level to retrieve content.
How much can your server do? Load testing capabilities work for web servers. Did you know that Perl CGI performs pitifully compared to C++ CGI? Test your server and find out which tools run most efficiently on your box. Don't create one of those "slow" sites!
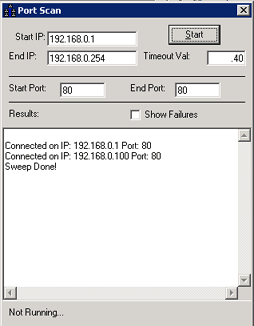
Scan one or more computers for open ports. The adjustable timeout value allows you to scan quickly or use a more thorough approach. These are full connection scans.
Be your own server!
Listen on any port!
You can listen on any port. This is similar to turning net cat on and listening for a connection, but with no unsafe flags and in a nice GUI environment. You can type back your responses to the client. Using the HTTP protocol, you can write directly to the client web page! This feature is great if you want to see what information your browser is submitting to a web server (change the action attribute on the form tag to "localhost").
Be a client!
Connect to any text based protocol server!
HTTP, FTP, SMTP, and others are all servers that utilize a text based protocol. If you know a bit about the protocol, you can use WebSpy to converse with the server. Once I wrote an HTTP server and used this utility to review the responses. It is very difficult to debug the HTTP protocol output of a web server by using a web browser. WebSpy presents the RAW information (un-rendered HTML along with the HTTP headers).
Bring your server to its knees!
Load tests are important!
When designing a web site, especially a site that uses server side technology (CGI, ASP, PHP, etc..), it is important to get an idea of how well the site performs and the number of concurrent users that it can support. The load test feature can start multiple threads (users) and make a defined number of requests to the page of your choice. When finished, you will get a report of the progress of each thread as well as the total time taken to complete your request.
Port scanning is rude!
Port scanning is an important aspect of Penetration Testing
When you want to know where your server (or any other computer) is vulnerable on the Internet, one way to get a clue where to look is by scanning for open ports. Scanning another network is considered rude (as they figure you are looking for weaknesses) but scanning your own computers is critical to maintaining a secure network. Using the port scan you can scan your box or the whole network. You can also adjust the timeout value to allow for a more thorough scan (which takes longer) or a quick scan (which is faster but can miss some ports). This doesn't use stealth scans (full connection only) simply because it isn't meant as a utility for un-ethical use.
|



